5 Essential Elements For jim cramer buy buy buy
5 Essential Elements For jim cramer buy buy buy
Blog Article

That’s for the reason that these “penny stocks” are commonly the playground for scam artists and market manipulators. If we ever do publish commentary over a minimal-volume stock that could possibly be affected by our commentary, we demand that InvestorPlace.com’s writers disclose this fact and warn visitors with the risks.
The chance that a participant will learn the solution is related to the network's whole mining capacity.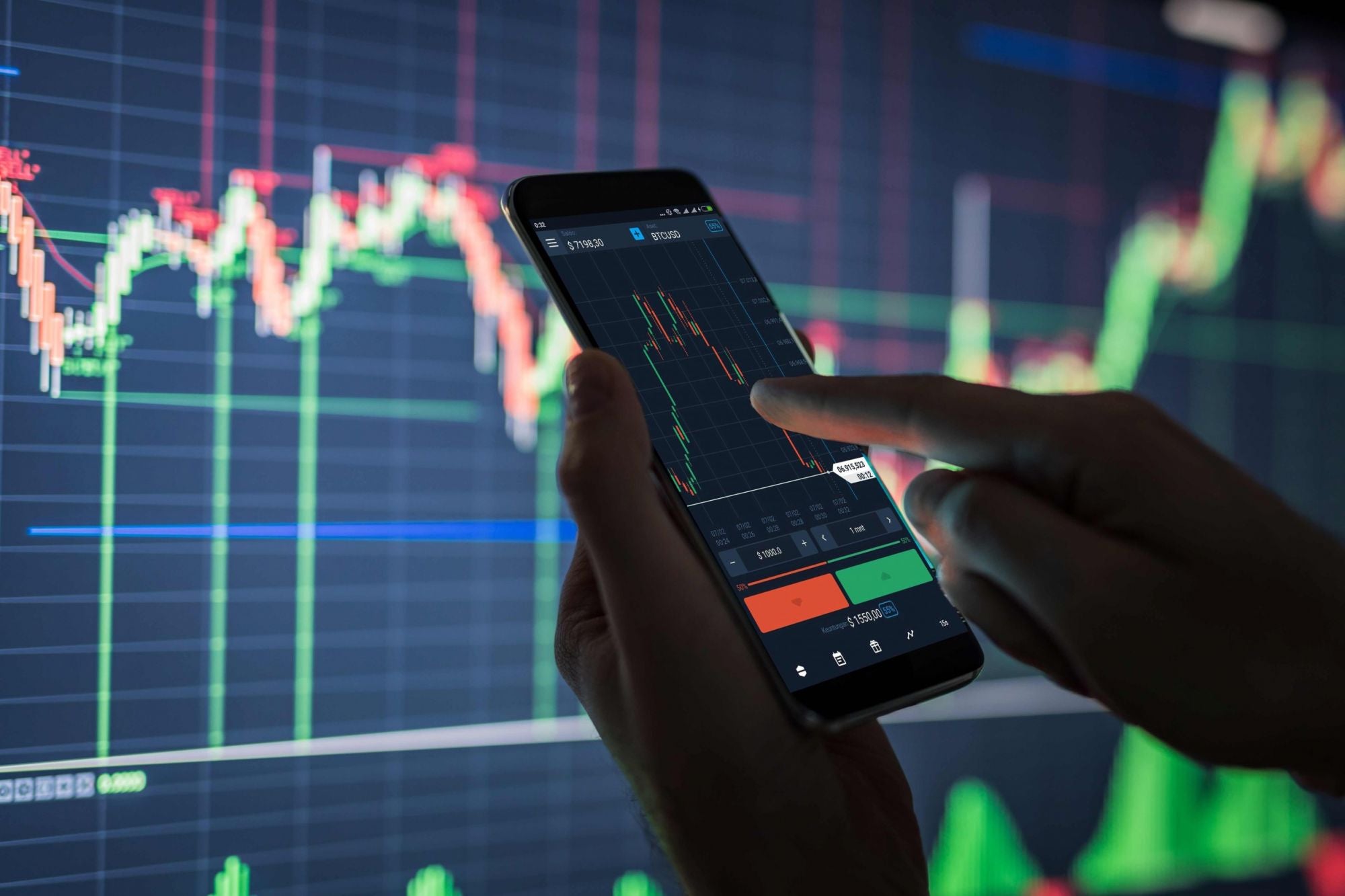
If not, it wouldn’t surprise me to get there by Wednesday. The situation obviously is that we have been getting quickly overstretched so it’s almost extremely hard to chase this market.
For more information on dividend distributions for this fund make sure you see our commonly questioned inquiries.
The next source of revenue for Bitcoin miners is the transaction fees that Bitcoiners really have to fork out when they transfer BTC to one another.
Your browser isn’t supported any longer. Update it to have the best YouTube experience and our latest functions. Learn much more
No matter whether you require short-term rentals or are searching for extra long lasting storage solutions Flex Storage provides affordable options without compromising on quality. Our services cater to the two, on demand storage requirements perfectly as People looking for extended periods of time.
The decoy serves as being a distraction for attackers, stopping them from identifying real and important data.
Defending intellectual property: Companies that need to shield their IP can use honeypots to distract and include attackers.
Ahead of committing to investing your time and energy and acquiring expensive machines, Read more to see no matter if mining is really for yourself.
The topics above have just scratched the surface of honeypot cyber security. If you want to learn more about honeypot security as well as other IT procedures, it’s an outstanding idea to deepen your understanding with a cybersecurity certification. EC-Council’s C
A Bodily honeypot, given that the title implies, is usually a Bodily IT system or process linked to a network with its possess IP address. Actual physical honeypots can reach greater verisimilitude but are website here less regularly applied a result of the Price tag involved.
We've been getting into an extremely disruptive interval in history. Even with Trump’s outstanding reforms, inflation is almost sure to return, as are QE and stimulus checks.
And we’re off ️ it’s been an excellent two days of meetings & learning. Thanks for joining us in Miami ☀️ #MinesandMoneyMiami
Best Url's:
https://financialtimes.com